Starshard-Reassembly
Starshard Reassembly Writeup
Table of Contents
1. Introduction
Starshard Reassembly is an easy challenge from HTB University CTF 2025: Tinsel Trouble.
2. First steps
We start by analyzing the provided file. A quick check reveals it is a Mach-O binary (macOS executable).
When I attempted to run the binary locally, I encountered an architecture mismatch error: zsh: exec format error: ./memory_minder
Since we don’t have access to the source code, the next step is static analysis. I opened the binary in Binary Ninja to inspect the disassembly.
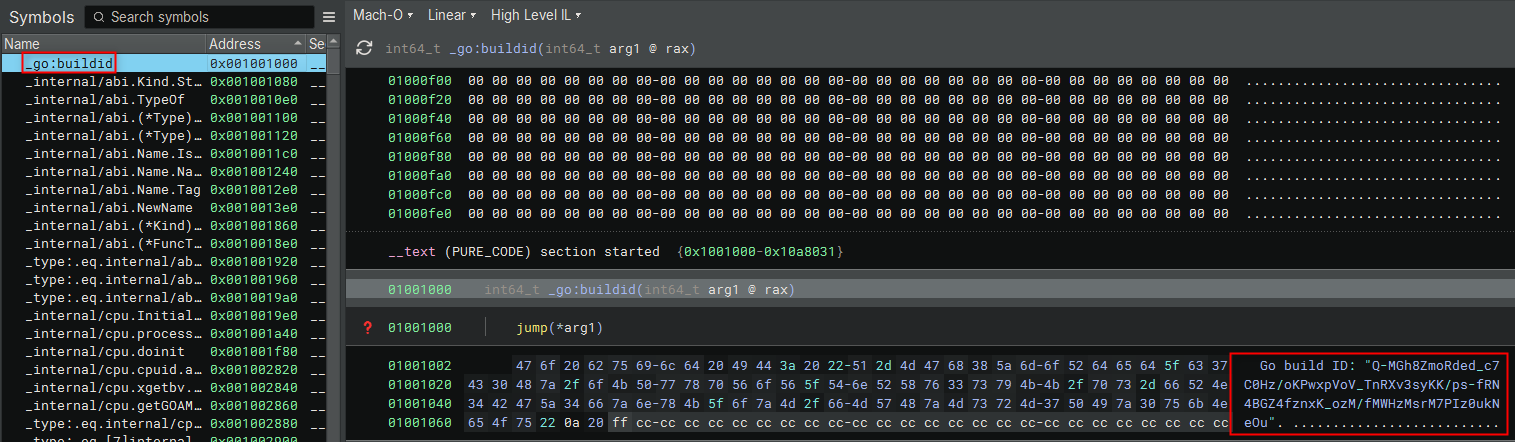
Upon loading the binary, the first thing we notice is the _go:buildid symbol. This confirms we are dealing with a Go binary.
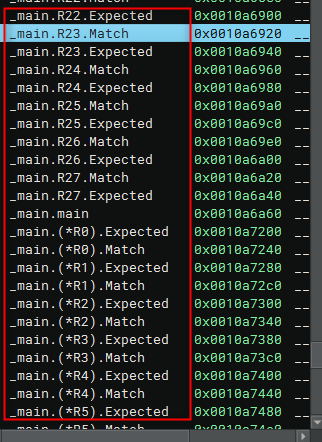
The binary has lots of different symbols, but after a quick check, it appears a pattern of names with the structure main.R0 to main.R27 with an implementation of Match and Expected for each one.
After reviewing both Expected and Match symbols, we can see Match compares a value and Expected returns another value.
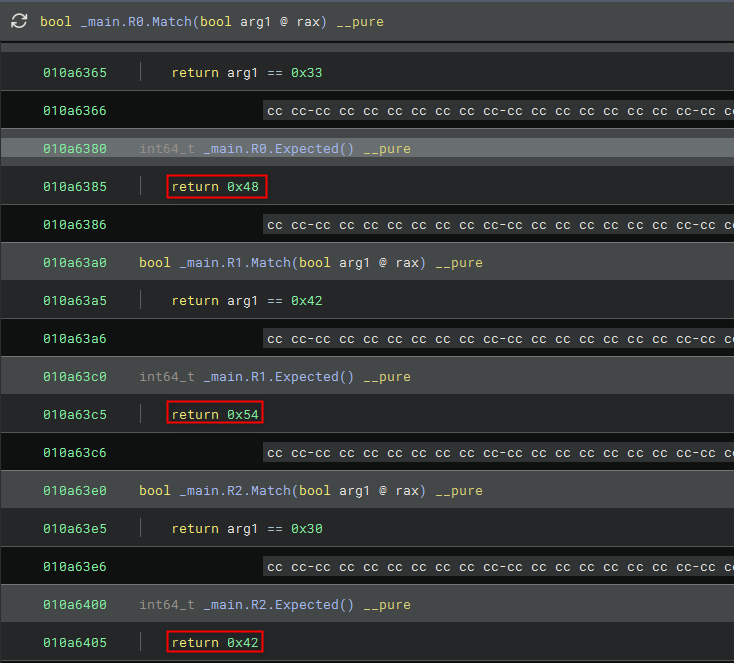
I analyzed the first few structs to understand the logic. Interestingly, there was a discrepancy between the Match and Expected functions:
main.R0.Match: Compares input against0x33(‘3’).main.R0.Expected: Returns0x48(‘H’).main.R0.Match: Compares input against0x42(‘B’).main.R1.Expected: Returns0x54(‘T’).main.R0.Match: Compares input against0x30(‘0’).main.R2.Expected: Returns0x42(‘B’)
Since the challenge flag format is known to be HTB{...}, 0x48 , 0x54 and 0x42 perfectly match the first three characters. This confirms that the Expected() method for each struct holds the correct byte of the flag.
3. Solution
To retrieve the full flag, we just need to iterate through R0 to R27 and extract the return value of their respective Expected functions.
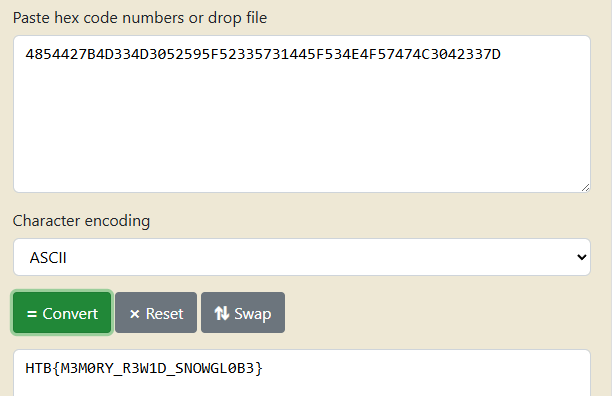
By collecting these values in order, we get the complete string:
Flag: HTB{M3M0RY_R3W1D_SNOWGL0B3}