Bypass
This is a .exe file that when we run it prompts for a terminal and asks for a username and password. First of all, we run strings on the binary.
Here, we can see the version of the file and after wasting some time debugging it with ida, I searched and found a tool called dnSpy which can be used to debug .NET binaries.
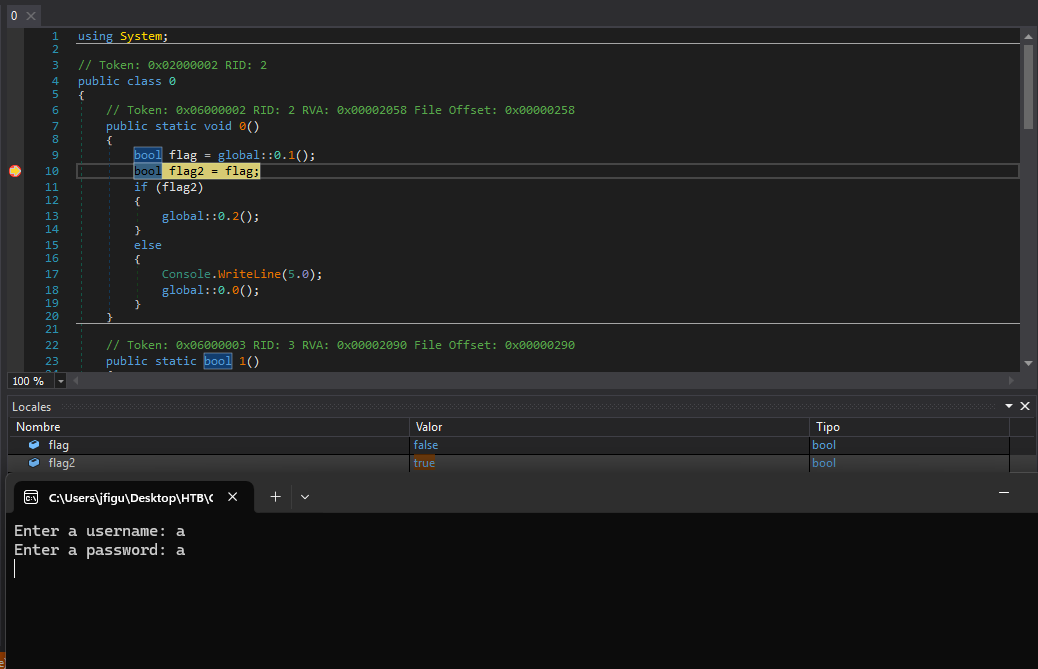
After learning how to use it, we find some functions. The first function has an if condition that we need to pass to make it to function 2(), we see that flag2 is the same as flag1 and that value comes from 1() which takes the input asked by the user.
1() always returns false so by adding a breakpoint and changing its value while debugging, we can pass this first check.
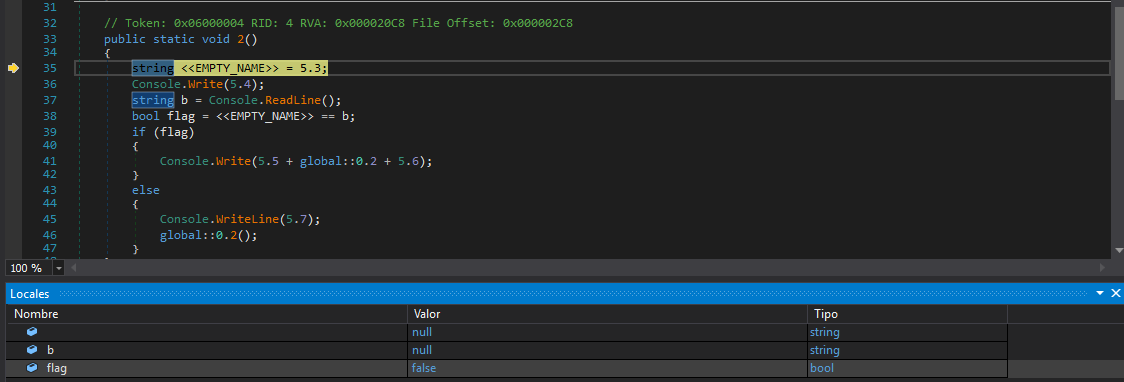
Now we land in 2(). Here, flag is true when our input b is equal to the variable <<EMPTY_NAME>>.
When debugging this, we can see the value of this variable is “ThisIsAReallyReallySecureKeyButYouCanReadItFromSourceSoItSucks”, so by passing this as input, we complete the challenge.